'Complete Control': Notorious Surveillance Contractor Tech Uncovered
- OurStudio

- Jun 26, 2014
- 2 min read

telegraph-screenshot
Hacking Team, a company which has been described as an "enemy of the Internet," provides law enforcement and intelligence agencies with legal "offensive technology" to infiltrate and remotely control people's phones and other digital devices. The extent of this company's capabilities remain murky, but two groups of Internet security experts say they have just exposed some of their surveillance firepower and the fact that Hacking Team has more servers spitting out malware based in the U.S. than any other country.
"Our latest research has identified mobile modules that work on all well-known mobile platforms, including as Android and iOS" as well as Windows Mobile and BlackBerry, announced the Russian-based Kaspersky Lab on Tuesday. "These modules … translate into complete control over the environment in and near a victim's computer." Indeed, the governments who use Hacking Team technology can turn on a cellphone's microphone, camera, and GPS unnoticed. They can also access people's email, call history, chats, browsing history, among many other potentially incriminating data.
"It's long been known that law enforcement and intelligence agencies worldwide use Hacking Team's tools to spy on computer and mobile phone users—including, in some countries, to spy on political dissidents, journalists and human rights advocates," explains Wired. "This is the first time, however, that the modules used to spy on mobile phone users have been uncovered in the wild and reverse-engineered."
Citizen Lab
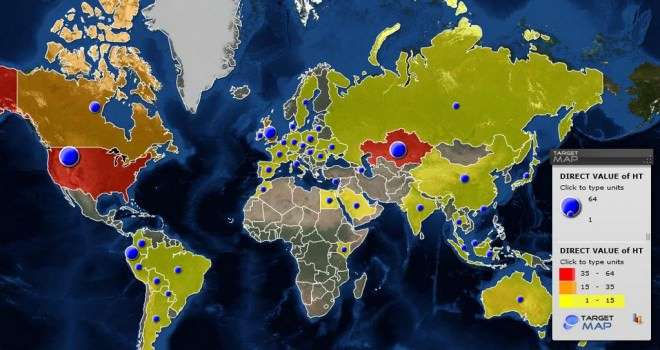
One of the biggest doozies of the Kaspersky Lab report is that the U.S., by far, houses the most Hacking Team servers, which are part of a "huge infrastructure that is used to control the [remote control system] malware implants." There are 64 known servers here, compared to 49 in Kazakhstan, 35 in Ecuador, 32 in the United Kingdom. Most of the other 40 countries that the lab traced Hacking Team malware back to have only one or two servers.
The lab cautions, "we can't be sure that the servers in a certain country are used by that specific country's LEAs [law enforcement agencies]; however, it would make sense for LEAs to put their [command and control servers] in their own countries in order to avoid cross-border legal problems and the seizure of servers." Likewise, it's no secret that the company has aggressively marketed itself to American government officials.
Hacking Team spokesman Eric Rabe quick to downplay the findings as "old news," according to the Associated Press. "We believe the software we provide is essential for law enforcement and for the safety of all in an age when terrorists, drug dealers and sex traffickers and other criminals routinely use the Internet and mobile communications to carry out their crimes," he assured.
However, Citizen Lab at the University of Toronto, which produced a report alongside Kaspersky Lab's and has long kept an eye on Hacking Team, reitereates that the company's products have a history of being used to target journalists and activists around the world.
"This in many ways is the police surveillance of the now and the future," cautions Morgan Marquis-Boire, a lead author on the report and a security researcher with Citizen Lab. "What we need to actually decide how we're comfortable with it being used and under what circumstances."




Comments